There’s also PasswordMaker which generates unique passwords for sites using a similar approach, just replacing the manual transforms with proper hashing algorithms. No passwords are stored anywhere, and you can acoomodate different rules for the silly sites that require rules to make their passwords less secure.
Not sure about other browsers, but with Chrome in particular, if I have physical unattended access to your PC, and you are storing all of your passwords in the browser, I have access to all of your passwords.
Hamburger -> Settings -> Advanced -> Manage Passwords
Then hover over any password you wish to see and click on ‘Show’.
I really wouldn’t recommend anybody to do this, use a good password manager (ie Keepass) and any time you get asked by the browser, click, “Never for this site”.
What if we add special characters, to keep Q*Bert happy?
And when you get sick of so many sites rejecting your password left and right, you switch back to alphanumeric. (I found that doubling the numeric probability also leads to more sites accepting your password.) Only a few require a symbol, mostly government, which can be appeased with a quick suffix. 12-14 alphanum sure beats 8-9 with symbol.
The more annoying are sites that require a username to pass their password validation. Prudential retirement requires a number in the username! That’s only the most recent insanity I’ve come across.
Why are we still beating a dead horse? Authentication with a username and password is bad and we should move ways that don’t require you to login to a site with just 2 things typed in editboxes.
Be it identityeservices or two-factor authentication. Something that is better then what we do now.
So I would state in these day, with all the sites I visit:
I need to remember too damn many passwords
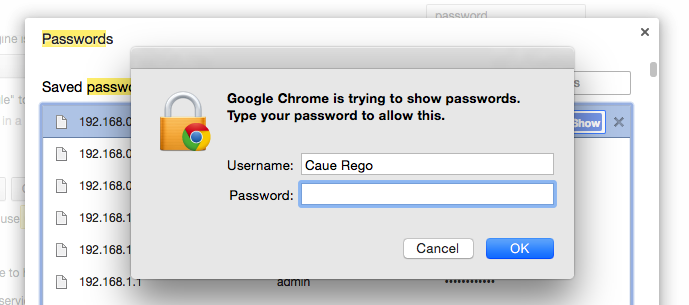
Interesting, but that does not work for me on Chrome latest. When I do the above I am prompted with this:

I use https://www.pixelock.com/ which generates random 15 character passwords that are computed every time you need them.
Ah, I don’t think that is out of the box behavior though, maybe you set this up in the past? Or might be a Windows UAC thing (my settings may be different to yours), not sure.
Couple of issues there, Jeff - as a user, I have learned over the years that WAY too many sites that simply don’t work if I use long/complex passwords. I’ve been trained by other people’s incompetance to keep it in the 8 character range and to not get fancy with the symbols. Most recently I encountered an on line store who let me set a 20 character PW no problem. But then wouldn’t let me use it to log in (I got errors from their back end). So NO, I don’t use passphrases - every time I try, it bites me in the ass.
The important thing is to keep the users from using the same PW everywhere, or get away from passwords altogether somehow. I use Google as a login, but I don’t really trust them much more than I used to trust MS, so I don’t use it everywhere.
The problem isn’t hash rates, Jeff, it’s trust and training.
the issue i have, is that most sites don’t deserve a long complicated password. email, banking, etc, of course. but when stupid blogs are asking me for A UNIQUE 12 character password, I simply won’t use their site.
developers seem to always think their site is deserving of crazy password security schemes, when most are not.
The problem still lies with the user, though, especially the people who do a lot of mobile computing. Longer, more complex passwords are more difficult and time-consuming to type into mobile keyboards, as you said in your article. Mandating a 12-character minimum, despite being great for security, is going to turn a lot of mobile users away.
It might be time for different forms of authentication to really take hold. Passwords were made in a time when the main way of inputting anything was your keyboard, but these days you can hardly find any computer without a touchscreen on it. Apple and Microsoft (and probably some other sites I’m forgetting) have made some advances: Touch ID for iPhones/iPods and Picture Password on Windows 8+. The latter is pretty pleasant to use on a mobile device with a so-so keyboard, although there might be some security concerns. It’s easier to remember, too, and at least Touch ID is a lot less vulnerable to brute-force attacks.
Like many have said, there are multiple things that Jeff is bringing up… users using better passwords, sites/systems that need to store usernames+passwords to do a much better job at what they are doing (and like many commenters have said - allowing much more complex passwords!! seriously what’s the problem here??) not to mention allowing reuse of some general authentication like Google/Facebook/etc.
Personally I retain all my passwords in a KeePass database (which has a master password which is pretty darn long) and by far most all of them are randomly-generated using the max of whatever the site allows. Unfortunately, so many of the sites restrict password length which is disappointing. Whatever is the max, I use it and if it allows special chars, I use them as well. That said, by far almost everyone I know (which a large percentage are IT geeks) thinks I’m nuts doing this… I can’t access my email/facebook/anything unless the device/computer is setup unless I specifically set the password to something temporarily for me to remember. Sucks but is secure. There’s shortcuts for the desktop, but not for mobile (or at least that I’ve figured out yet). Eh… it has its pain points.
But yeah most people really just don’t care … and how to get that to change? Frankly, those people are generally not going to be reading this blog…
What do you think about 2-step verification? I use that on all my important accounts, when it’s supported.
The problem with low-security passwords on forums and comment sites is password reuse. You are well above the curve simply by having different passwords for different accounts. But a lot of users simply use one or two passwords for everything. That’s why the best password is no password at all.
For throwaway accounts, especially ones where you don’t even care to use your name (or commonly-used user name), use www.fakena.me. It generates a random identity with a working email account that exists long enough to register + confirm an account, then disappears.
On paper, it seems pretty OK to trust other software to manage your passwords, but you should always be very careful. Look at this open issue in Chrome:
https://code.google.com/p/chromium/issues/detail?id=138147
It’s been there for almost three years…
In my personal case, I use KeePass2 with the AutoType option (either through AutoKey or AutoHotKey if you use windows). That way I never type a password, I am sure they are encrypted and I never have to generate a password myself.
And that’s the problem. There is no way to detect reuse. So if they start forcing complex passwords on blogs, the response will be to use the same single complex password they can remember everywhere.
“Stop requiring passwords altogether”, then say just use any of the other sites that require a password and can be hacked, might have weak passwords, etc.
A 1-factor authentication using my phone (which I have with me) so clicking “login” will send a text or a voice generated phrase I would need to type in as a one-time session password fixes all this, but few use it except for initial authentication. I could even use a “burner phone” separate from my main phone to avoid theft or loss.
For a better cabalistic number which will last longer, I’d say 16. Think length needed in at least 2 years to come, as you even implied later on:
On top of this, technology evolves not just following the self fulfilling moore’s law, but also in almost unpredictable ways. What we can predict is that it’s reliable to believe it will most likely improve more than linearly and by 2019 it’s much more likely it will be much less than 2 days to crack a 11 characters password. Maybe even as little as a few hours. So, in less than 4 years using 12 length will be already a “thing of the past”. Why not simply preventing that by adding just a few characters to the recommendation sooner than later?
16 it is for myself. ![]()
Also I’ve missed other 2 recommendations on the article:
-
How about accounts you want to share with someone? Granted, all accounts should be personal and exclusive, but that’s again not a real expectation from users. They share accounts and now sharing a google account password just to give access to a minor website might soon become an issue.
-
How about going on other devices? That’s simple enough, as some argued, using 2 factor authentication. But that’s quite an annoyance and not as simple as having a simple password you always remember to type in.
Some accounts will always be low risk. So just use a regular week password and fuck it, as many said already.
I’d also argue there are some even lower risk that don’t even need a password to begin with. Just use gravatar and let anyone claim it’s you, since it won’t matter if anybody tries to impersonate you. Example? Making a service order to send in a repair item. Proof? I’ve actually done this in 2004 and the business still exists up to today. Customers make orders with a saved profile just by typing their Tax ID. It just works.
Not really a problem since that’s just not true thanks to the wrong qualifier there: never.
This is the default behaviour here right now, and it is pretty much just authentication in my book:
So true. But I find it so much easier to simply type my one good and strong google password anywhere I go to access anything I need rather than making a medium 12 character secure password just so I can remember it when I want to go outside my devices. Not to say there isn’t some usage cases, as I’ve mentioned up there.
That triggered me to wonder into this (probably stupid) question: does Discourse use #3 only if you do generate a password?
On a side slightly funny easter eggy note… Recently I stumbled upon www.simple.com an interesting banking concept which unfortunatelly is US only. It was the first time I’ve seen a business referencing the should-be-obligatory xkcd (also used in this article) using it as an example. I couldn’t find a simple way to screenshot it since account creation is only through invitation, but here’s a post from another person who noticed it. The funny thing is that they did accept correcthorsebatterystaple it as my password (and until now I didn’t even knew they tried to block it)! Talk about insecure measures! ![]()
I could have set something for me too, but I don’t remember it. And I get same behavior than Jeff:
It’s both. As you said yourself earlier, too many sites simply don’t work properly. You need hash rates first, trust and training later.
Here’s a wild thought. What if one or more of the major “key-ring” sites, such as Facebook, stopped letting users generate their own passwords? Just create a list of, say, twenty secure passwords and have you choose one. If you want to change it, then here’s another twenty to choose from (but you can’t ask for a refresh, because those twenty should be good enough for anyone).
Ideally, these suggestions would all be xkcd-style phrases, due to the advantages of those. And I sort-of disagree that passphrases are annoying on mobile devices. For one thing, it’s tricky to hunt around for the special characters on those tiny keyboards, but simply typing whole words is something we have frequent practice with, espeically when we have to use words outside the phone’s dictionary.
Which brings me to my second idea. If mobile operating systems and applications didn’t apply the wrong sorts of paranoia to password fields, then we could take advantage of the strides in mobile keyboards. Firstly, as many others have said, passwords may as well be unmasked under most circumstances. And furthermore, why not the option to “swype” your password (or whatever Android calls it now)? If your phone already has a large dictionary that includes the words “correct”, “horse”, etc, then what is lost security-wise in being able to spell out CorrectHorseBatteryStaple in four gestures, just like if I were texting the phrase to a friend?
I would much rather see users have one master login on Facebook or Google with a long, unique password and behind two factor authentication – because lots of sites with mostly reused, simple 8 - 12 character passwords, all of them using weak hashes and just waiting to have their user database downloaded and hash cracked someday en masse is far, far more dangerous!
(There is really no difference between using Lastpass or whatever and Google as your single source of auth. If someone cracks your Lastpass password you are just as hosed.)
I also trust Facebook and Google a lot more than other random websites, even banking ones…